Running a WordPress website can be exciting, but it also comes with serious security challenges. Implementing WordPress DDoS protection is crucial, as Distributed Denial of Service attacks can overwhelm your site, slow it down, or even cause downtime.
Table of Contents
-
Introduction — Why WordPress Sites are Targets
-
What is a DDoS Attack?
-
Signs Your WordPress Site is Under Attack
-
How to Confirm a DDoS Attack
-
Emergency Steps to Stop a DDoS Attack
-
Long-Term DDoS Prevention for WordPress
-
Tools and Plugins for Protection
-
Step-by-Step Implementation Example
-
Case Study
-
FAQs
-
Conclusion
1. Introduction — Why WordPress Sites are Targets
WordPress powers over 45% of all websites worldwide. Its popularity makes it a prime target for hackers, botnets, and malicious actors. DDoS attacks can:
-
Overload your server
-
Crash your site
-
Impact user experience
-
Negatively affect SEO
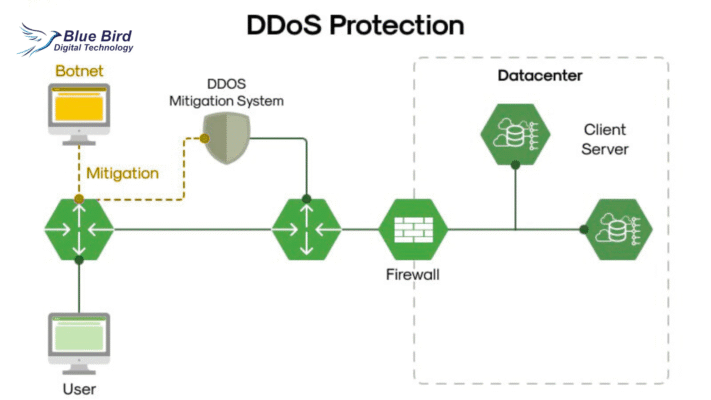
2. What is a DDoS Attack and How WordPress DDoS Protection Helps
A DDoS attack occurs when multiple compromised systems (bots) flood a website with traffic, overwhelming the server’s resources.
Example:
Imagine a small coffee shop receiving 10,000 orders per minute — legitimate customers cannot get served, staff is overwhelmed, and operations fail. That’s exactly what a DDoS attack does to a website.
[Image suggestion: Flowchart of DDoS attack — attacker → botnet → website → server crash]
Types of DDoS attacks:
-
Volumetric – Overwhelms bandwidth (UDP floods, ICMP floods).
-
Protocol – Exploits server resources (SYN flood, Ping of Death).
-
Application Layer – Overloads specific applications like WordPress login pages.
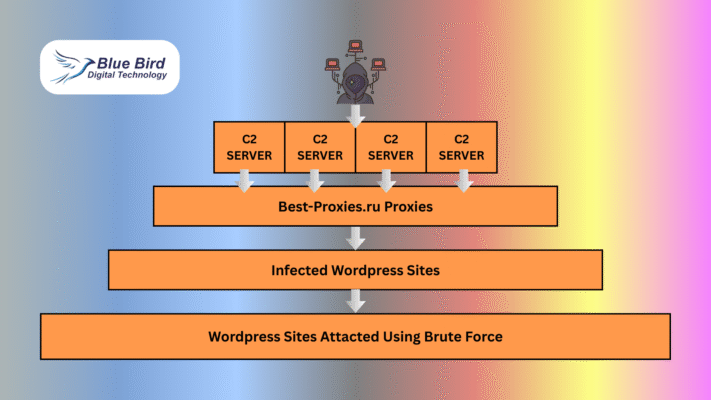
3. Signs Your WordPress Site Needs DDoS Protection
Check for:
-
Sudden slowdown or site unresponsiveness
-
Spike in 5xx errors (502, 503)
-
Abnormal CPU/memory/network usage
-
Traffic anomalies in analytics
-
Repeated access to
/wp-login.phpor/xmlrpc.php
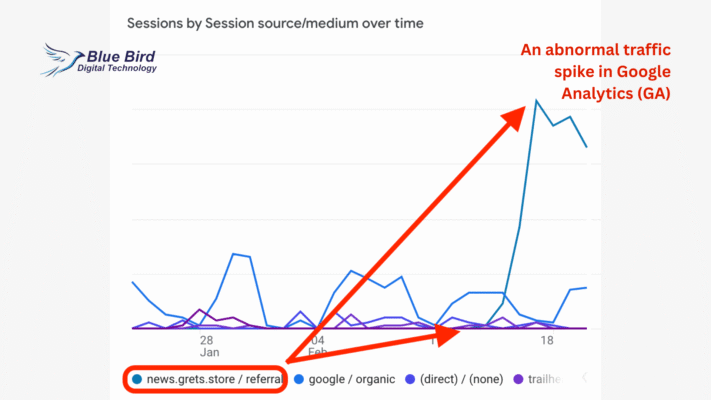
4. How to Detect a DDoS Attack on WordPress
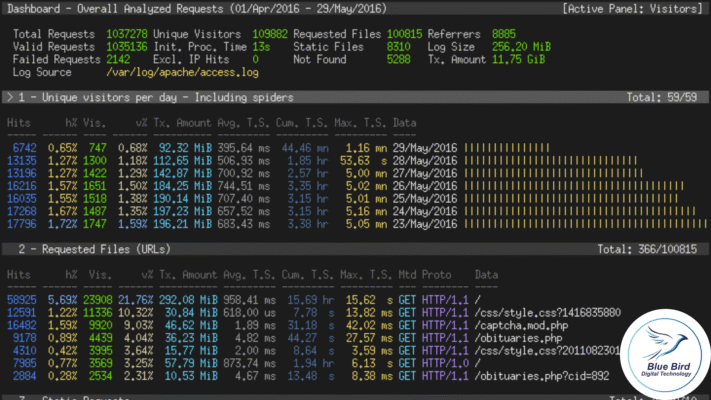
-
Check Uptime Monitoring Alerts — UptimeRobot, Pingdom
-
Analyze Server Logs — Identify high-frequency IPs
awk '{print $1}' /var/log/nginx/access.log | sort | uniq -c | sort -nr | head
-
Look for Suspicious Patterns — Repeated requests, non-existent pages, or unusual user agents
-
Compare Analytics vs Logs — If GA shows fewer users than logs, traffic is likely fake
-
Check Host/CDN Dashboards — Many managed hosts highlight abnormal spikes
5. Emergency Steps to Stop a DDoS Attack on WordPress

-
Enable Cloudflare Under Attack Mode
-
Use DNS-level WAF (Cloudflare, Sucuri, Imperva)
-
Block malicious IPs and countries
-
Apply rate limiting for
/wp-login.phpand/xmlrpc.php -
Temporarily disable vulnerable endpoints
-
Contact hosting provider for emergency support
6. Long-Term WordPress DDoS Protection Strategies
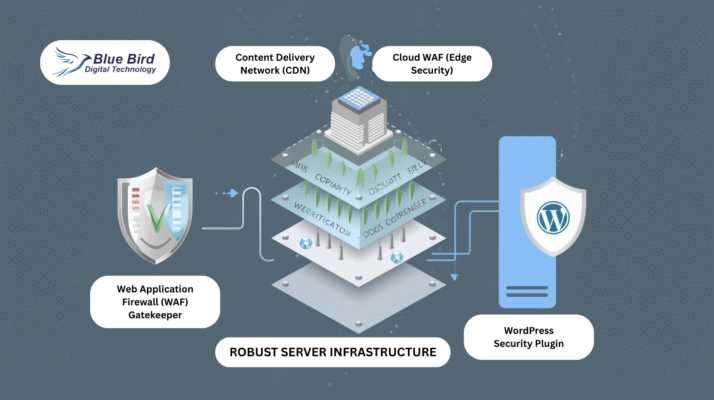
6.1 CDN + WAF
-
Cloudflare (Free/Pro)
-
Sucuri WAF
-
Imperva Incapsula
6.2 Hosting Infrastructure
-
Managed WordPress hosting with DDoS protection
-
Auto-scaling server resources
6.3 WordPress Plugins
-
Wordfence
-
iThemes Security Pro
-
All-in-One WP Security
6.4 Caching & Performance
-
Server-level caching (Nginx FastCGI, Varnish)
-
WordPress caching plugins (WP Rocket, LiteSpeed Cache)
6.5 Limit Login Attempts & Enable 2FA
-
Protects against brute-force attacks
-
Adds extra layer during a DDoS attempt
6.6 Disable/Restrict XML-RPC
7. Top Tools and Plugins for WordPress DDoS Protection
| Tool/Plugin | Function | Free/Paid |
|---|---|---|
| Cloudflare | CDN + WAF + Under Attack Mode | Free + Pro |
| Sucuri | WAF, DDoS mitigation | Paid |
| Wordfence | Application firewall, login protection | Free + Premium |
| iThemes Security | Login hardening | Paid |
| UptimeRobot | Downtime monitoring | Free + Paid |
| New Relic / Datadog | Performance monitoring | Paid |
[Image suggestion: Screenshot of Wordfence dashboard with firewall active]
8. Step-by-Step WordPress DDoS Protection Implementation
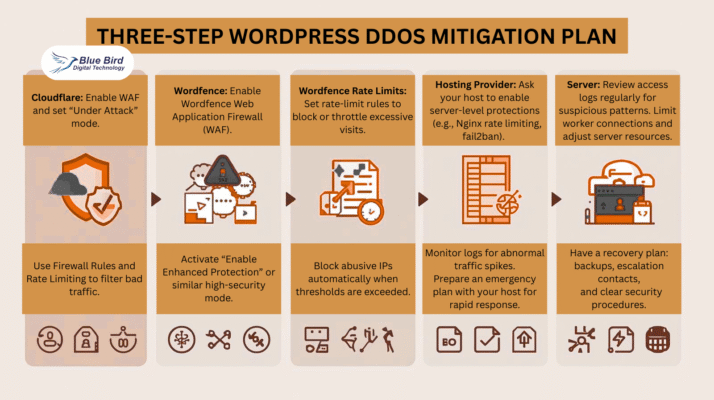
-
Cloudflare: Enable WAF + “Under Attack” mode
-
Wordfence: Enable login security and rate limiting
-
Host: Restrict abusive IPs/ASNs
-
Server: Enable caching and optimize Nginx worker connections
-
Emergency plan: Keep logs, contact host, escalate if needed
9. FAQs About WordPress DDoS Protection
-
Site: Medium eCommerce WordPress store
-
Attack: 10 million requests in 30 minutes targeting
/wp-login.php -
Solution: Cloudflare + rate limiting + Wordfence + geo-block
-
Result: Attack mitigated, legitimate traffic unaffected
10. FAQs
Q1: Can a plugin alone protect my WordPress site from DDoS?
A: No, large DDoS attacks require network-level protection like Cloudflare or Sucuri.
Q2: How do I differentiate between DDoS and genuine traffic spikes?
A: Check session duration, bounce rate, and IP patterns in logs vs analytics.
Q3: Will free Cloudflare handle all attacks?
A: Free plan protects against small/medium attacks. Large attacks may require Pro/Business plans.
Q4: Should I block countries during an attack?
A: Temporarily yes, if your audience is localized.
Q5: Can DDoS attacks harm SEO?
A: Yes, downtime and slow site speed negatively affect Google rankings.
[Image suggestion: FAQ section with icons for each Q&A]
11. Conclusion
DDoS attacks are inevitable but preventable with layered security.
-
Use CDN + WAF
-
Harden WordPress with plugins
-
Monitor logs and traffic
-
Prepare an emergency plan
The key: you can’t stop the attack entirely, but you can make your site resilient enough to survive it.
Along with keeping your site secure, speed is equally important.
Check out this guide to make your website faster:
Improve WordPress Site Speed 2025

Wow, this guide really breaks down DDoS protection in simple terms. I didn’t realize how vulnerable WordPress sites could be until now. Thanks for including both free and premium solutions!
ya you are right
Very informative post! I’ve been struggling with sudden traffic spikes lately—turns out it might actually be a small-scale DDoS attack. Gonna try those rate-limiting plugins you suggested.